Throughout this article, we will explore the best practices for securing online marketing initiatives, highlighting the strategic alignment of cybersecurity with marketing goals.
We will talk about the protection of customer data, managing third-party risks, incident response planning, and compliance. The following article is going to greatly enhance your understanding of proactive management in the cybersecurity domain and how to implement a complete security strategy within online marketing.
The Cybersecurity Imperative in Online Marketing
Where this digital domain brings unprecedented opportunities for marketers, it is also riddled with associated risks. Very serious consequences can be brought about by cybersecurity breaches—the average cost of a data breach is pegged at a staggering million. For small businesses, this can go to the extent of saying they close within six months after falling victim to a cyber attack.
In the year 2020, there were approximately 1,001 data breaches in the United States. As a result, over 155.8 million people were affected by data breaches in the same year. Aligned security practices blend in with the marketing objectives to engender trust with your audience, secure sensitive data, and maintain a competitive edge in the digital marketplace.
Securing Customer Data: The Foundation of Trust
At the heart of any successful online marketing initiative lies customer data. Protecting this valuable asset is not just a legal obligation; it’s a cornerstone of building and maintaining customer trust.
Utilize Advanced Data Protection Measures
Build secure backup systems and disaster recovery plans to put your cybersecurity strategy above the basics. This is in consideration that you should back up all your critical data regularly to secure, off-site locations so that businesses can stay running in case of a breach or other disaster.
Beyond employing basic security protocols, it’s critical to engage in advanced protection strategies to guard against sophisticated threats. This involves the implementation of industrial cybersecurity measures to secure sensitive data against emerging cyber threats.
Implement Robust Data Protection Strategies
The protection of customer information calls for strong security measures in place. All sensitive information must be well-encrypted at any given time, whether in transit or at rest. Put up strict access controls and authentication to restrict data access to authorized personnel only.
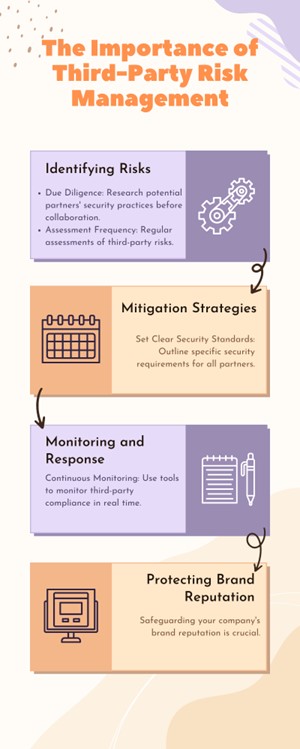
Third-Party Risk Management
Third-party risk management is a need of the hour in today’s interconnected digital world where organizations are reporting breaches that emanate from third-party vulnerabilities.
Proactively harden your security through the performance of end-to-end third-party risk assessments, such as due diligence on new partners and assessment of the security posture for ongoing third-party relationships at periodic intervals.
Furthermore, establish stringent security requirements and practices for all external collaborations. For mitigation of the vulnerabilities originating from third parties, design stringent vetting procedures, audit, and continuously update permissions, and deploy monitoring systems that raise flags on suspicious activities.
Implementing Effective Incident Response Plans
Despite your best preventive efforts, the possibility of a security incident remains. Having a well-structured incident response plan can significantly mitigate the impact of a breach.
Establish a Specialized Response Team
Create a dedicated incident response team comprising:
- IT security specialists
- Legal experts
- Communications professionals
- Key stakeholders from various departments
Define Clear Procedures
Develop clear, step-by-step procedures for:
- Identifying and classifying security incidents
- Containing and mitigating the impact of breaches
- Communicating with affected parties and stakeholders
- Investigating the root cause of incidents
- Implementing corrective measures to prevent future occurrences
Regular Testing and Updates
- Conduct regular simulations and tabletop exercises to test your incident response plan.
- Update the plan based on lessons learned from these exercises and real-world incidents.
- Stay informed about emerging threats and adjust your response strategies accordingly.
Compliance and Regulatory Adherence
Compliance in today’s data protection regime, especially under the GDPR and CCPA, is not a simple checkbox to tick off the legal list; rather, it is a competitive differentiator. Enterprises should continue refreshing their knowledge of applicable laws from time to time and incorporate these requirements into their marketing strategy.
This can be ensured by engaging a compliance officer who is very well-versed in these laws. There should be transparency towards customers; privacy policies have to be drafted clearly, and it goes right up to a more customer-friendly data management system, telling them how they can keep their data in control.
Also, it is the regular communication in data protection practices that will instill confidence. After all, 79% of consumers like transparent brands. In sum, compliance can do more than just prevent fines; it also secures customer loyalty.
Regular Training and Awareness Programs
Employees are the linchpin in cybersecurity; they are the first line of defense but can themselves be a risk if they are not properly trained. Comprehensive cybersecurity training is indispensable and should be conducted regularly.
This should include phishing detection, safe browsing, handling sensitive data, strong passwords, and multi-factor authentication. You can make these training sessions more effective by customizing them for the different roles in your marketing team. Besides this, instill a culture of security awareness.
Make sure employees are free to share information about possible security threats and, in that respect, encourage them by rewarding the employees identified or reported to have a risk. Regularly inform employees of the latest cyber threats and best security practices.
Monitoring and Updating Security Measures
The cybersecurity landscape is constantly evolving, and your security measures must evolve with it. Continuous monitoring and regular updates are crucial to maintaining a robust security posture.
Implement Continuous Monitoring
- Across all marketing channels and technologies, implement advanced threat detection systems.
- Use artificial intelligence and machine learning tools to pinpoint behavioral patterns indicative of anomalous activities.
- This security operations center will need to run 24/7 to respond to threats in real time.
Regularly Update Security Protocols
- Keep all software, systems, and applications current with the latest security patches.
- Run regular vulnerability assessments and penetration testing exercises.
- Stay ahead of emerging threats and change the security strategies accordingly.
Comparison: Traditional vs. Modern Security Approaches in Online Marketing
To better understand the evolution of security practices in online marketing, let’s compare traditional approaches with modern, more comprehensive strategies:
Aspect | Traditional Approach | Modern Approach |
Data Protection | Basic encryption and firewalls | Advanced encryption, AI-powered threat detection, and comprehensive data governance |
Third-Party Risk | Limited vetting of vendors | Continuous monitoring and rigorous assessment of all third-party relationships |
Incident Response | Reactive, ad-hoc responses | Proactive, well-rehearsed incident response plans with clear roles and procedures |
Compliance | Checkbox approach to meet minimum requirements | Integration of compliance into all aspects of marketing strategy and operations |
Employee Training | Annual or bi-annual general security training | Regular, role-specific training with simulated phishing exercises and awareness campaigns |
Security Updates | Periodic updates based on fixed schedules | Continuous monitoring and real-time updates to address emerging threats |
Conclusion
Strong cybersecurity in digital marketing efforts benefits the organization in protecting itself, but most importantly, the customers. It will help marketers secure data, take risks to a minimum, and build a reputation regarding the brand when fully supported by a solid cybersecurity strategy.
Online marketing security is not a one-time implementation. Strive to be alert, learn, and adapt to your strategies to stay ahead of emerging threats.
Frequently Asked Questions (FAQs)
What are the most effective online marketing strategies?
Some of the most effective strategies are content marketing, search engine optimization, paid advertisements, social media engagement, and email campaigns.
What are the 5 main strategies of digital marketing?
Key strategies include SEO, content marketing, social media marketing, PPC, and email marketing.
What best practices strategy can be identified for successful digital marketing?
Digital marketing to be successful should incorporate the key elements of generating high-quality content regularly, search engine optimization, active social engagement, utilizing data analytics for various insights, and personalization of messages to the target audience.

